Setting up Wazuh for Monitoring Failed Login Attempts on Azure
Project Overview:
This project involves the deployment of an Ubuntu-based virtual machine (VM) on Microsoft Azure, installation of Wazuh (an open-source security monitoring tool), and configuration of a Windows virtual machine (VM) to simulate failed login attempts. The goal is to monitor and analyze these failed login attempts using Wazuh’s advanced security capabilities. The final objective is to create a Wazuh dashboard to display the frequency of failed login events, providing valuable insights into the security status of the infrastructure.
Key Technologies:
Azure: Cloud platform for hosting the virtual machines.
Ubuntu: Linux distribution used for hosting the Wazuh manager.
Wazuh: Security monitoring platform for collecting, analyzing, and visualizing security data.
Windows Server: Simulated environment for failed login attempts.
Kibana: Visualization tool integrated with Wazuh to display security data.
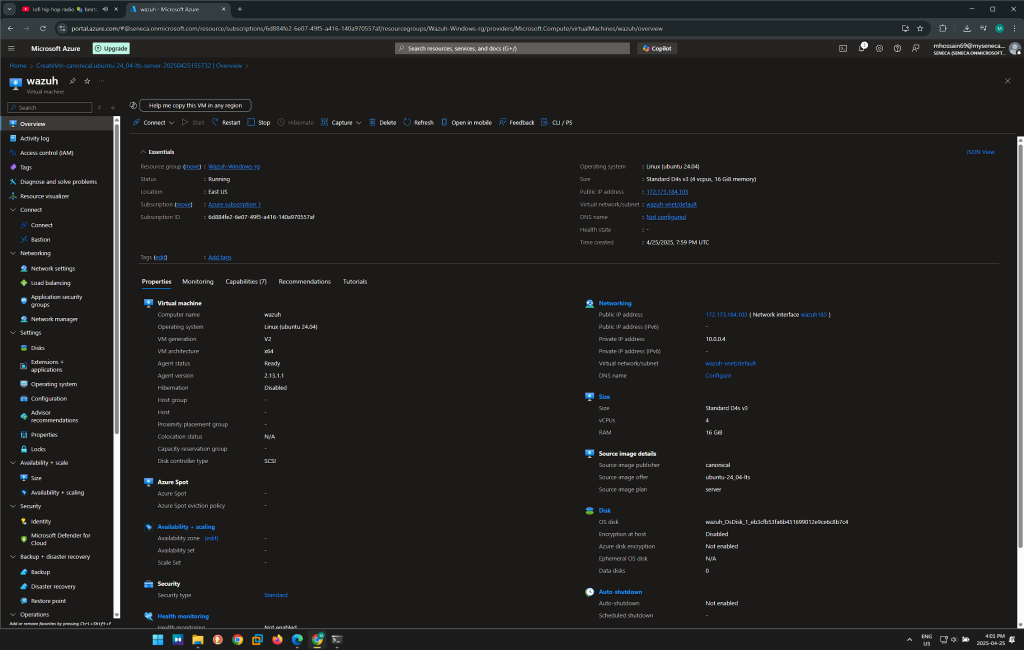
Objective 1: Set up an Ubuntu Virtual Machine on Azure
Action:
- Launch an Ubuntu VM on Azure by choosing desired size, region, and authentication method (use SSH for secure access).
- Open port 22 for SSH access and create the VM.
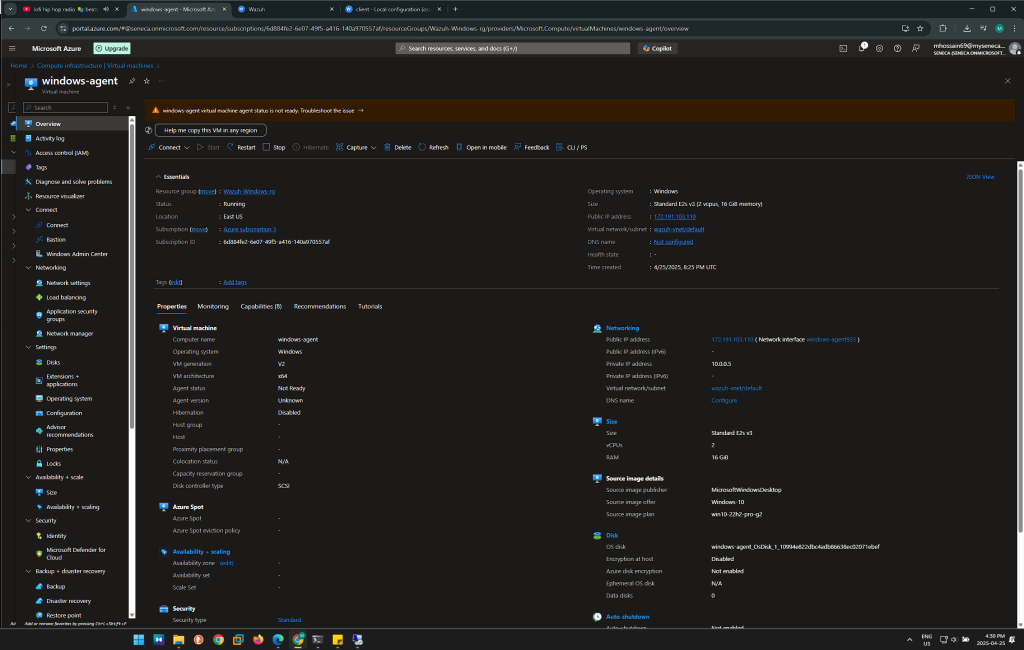
Objective 2: Set up a Windows Virtual Machine on Azure
Action:
- Create a Windows 10 VM on Azure by following the same process as the Ubuntu VM setup.
- Enable RDP (Remote Desktop Protocol) for remote access.
- Open the required to allow RDP traffic.
Objective 3: Install Wazuh Manager on Ubuntu VM
Action:
- SSH into the Ubuntu VM
- Update the package list
- Install Wazuh by adding the Wazuh repository
- Start and enable Wazuh Manager
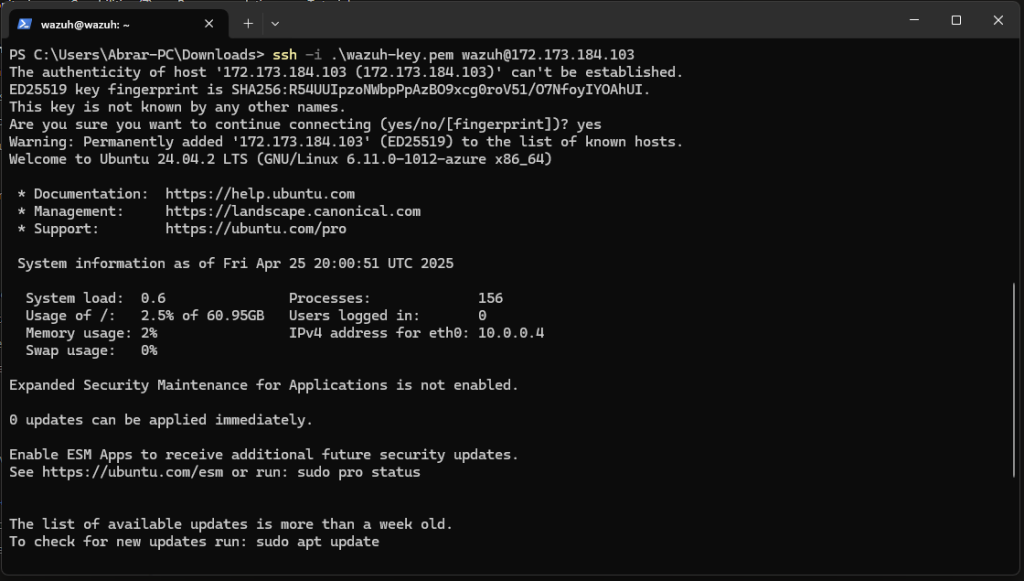
SSH into the Ubuntu VM:
ssh -i .\wazuh-key.pem wazuh@172.173.184.103
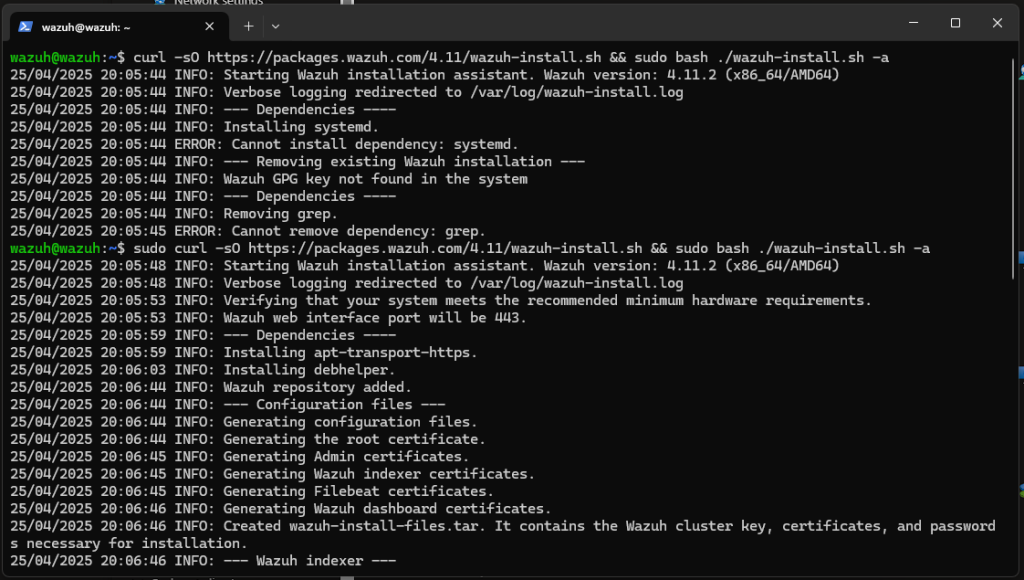
Install Wazuh by adding the Wazuh repository
sudo curl -sO https://packages.wazuh.com/4.11/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
Start and enable Wazuh Manager
sudo systemctl start wazuh-manager
sudo systemctl enable wazuh-manager
sudo systemctl status wazuh-manager

Objective 4: Log in to Wazuh Dashboard
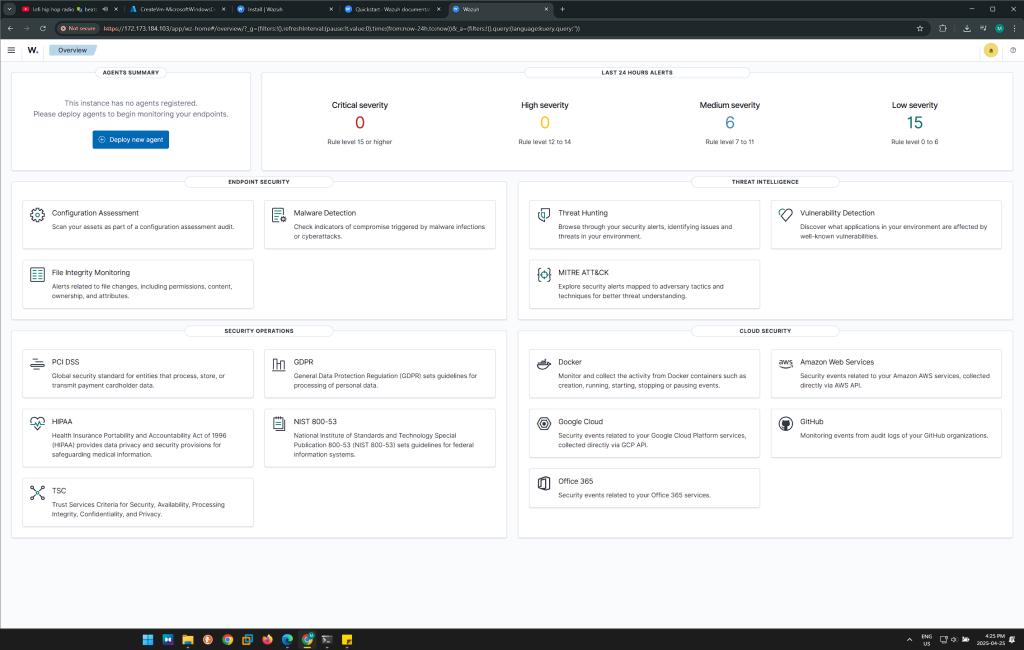
Objective 5: Install Wazuh Agent on Windows VM
Action:
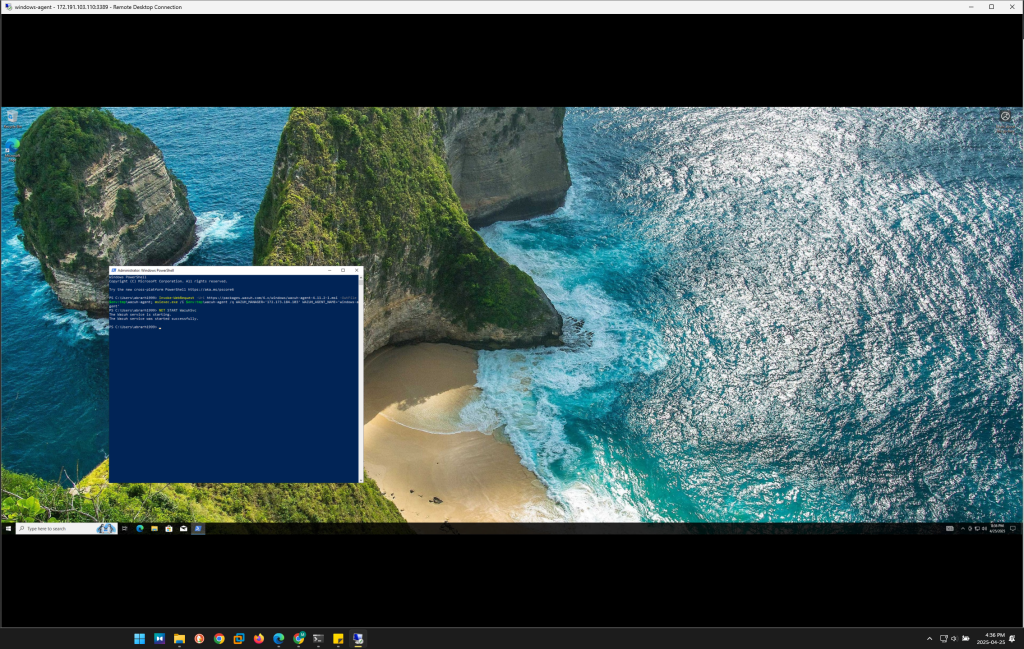
- Follow the instructions and configure the agent by specifying the IP address of the Wazuh Manager
- Start the Wazuh agent
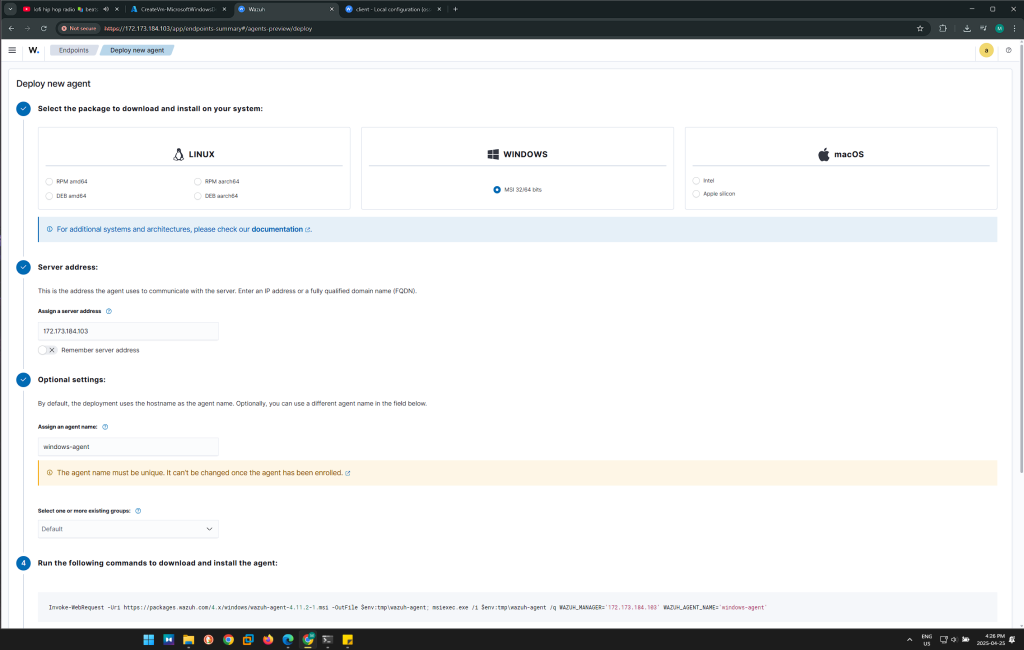
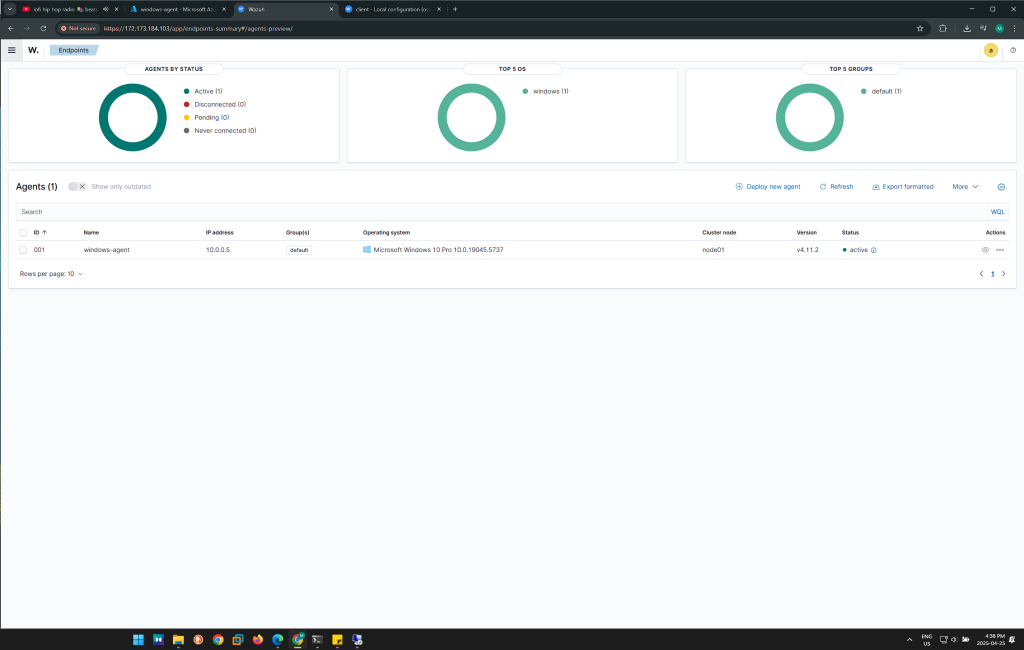
Objective 6: Generate Failed Login Attempts on Windows VM
Action:
- Use RDP to access the Windows VM
- Attempt to log in multiple times with incorrect credentials, intentionally triggering failed login events.
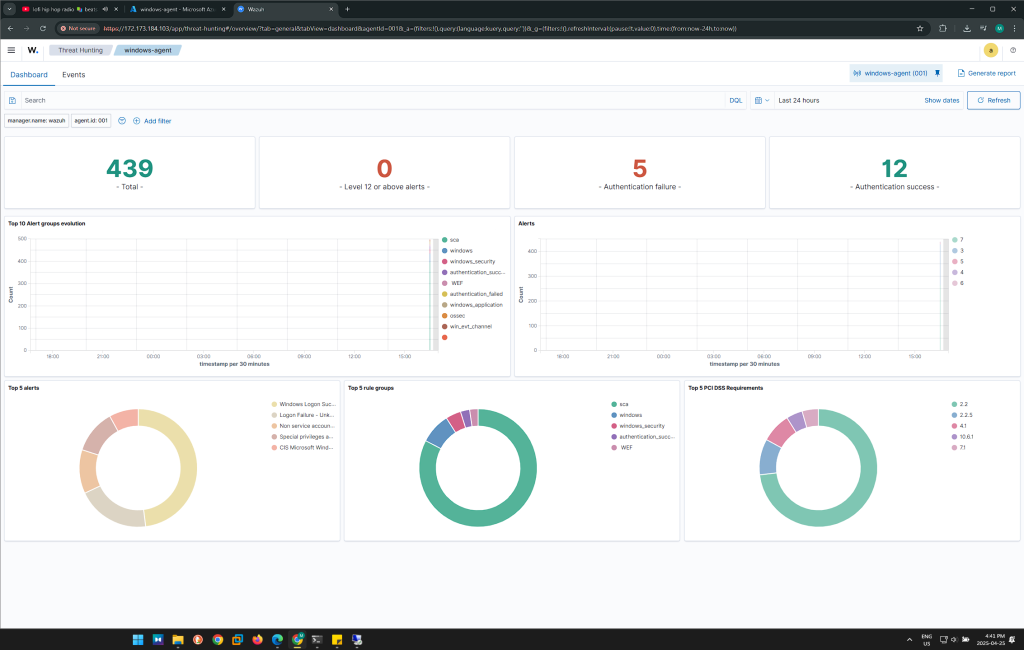
Objective 7: Access Threat Hunting and Filter code 4625
Action:
- Click on the Windows agent
- Then access Threat Hunting
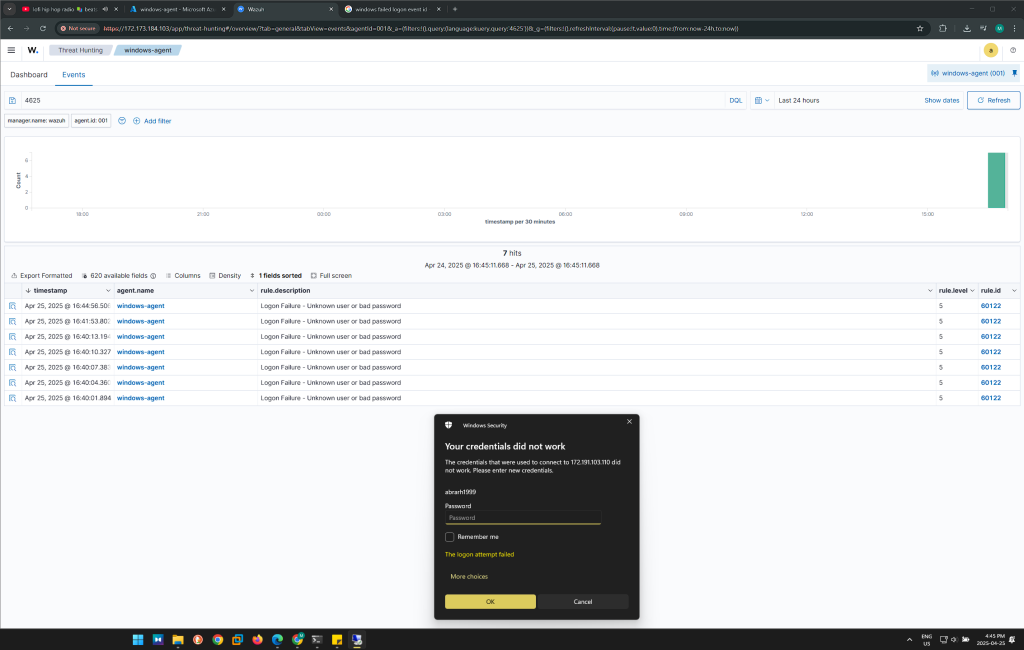
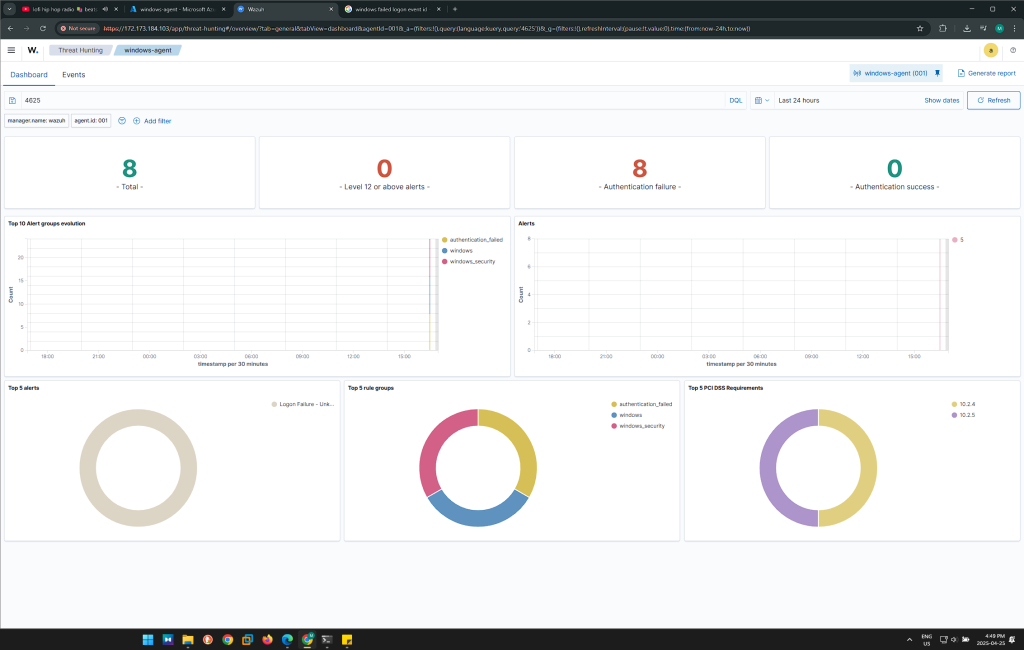
As I was entering wrong credentials, the failed login attempt went up from 5 to 7 hits. Finally, I tried again and it reached to 8 hits.
Project Outcome:
- Security Monitoring: The system now provides real-time monitoring of failed login attempts on a Windows machine, with Wazuh capturing the events.
- Visualization: The Wazuh dashboard provides an intuitive interface for tracking login attempts and security events, making it easier to analyze and act on potential threats,
Conclusion:
By completing this project, I have demonstrated my ability to:
- Deploy and configure cloud-based infrastructure using Azure.
- Set up and integrate security monitoring tools like Wazuh.
- Implement real-time monitoring of security events and generate actionable insights through visual dashboard.
This project highlights my skills in cloud infrastructure, security monitoring, and data visualization, showcasing a comprehensive approach to managing system security.