Windows Virtual Machine Hardening on Azure
Introduction
In today’s digital landscape, the security of cloud-based infrastructure is paramount, and the Windows Virtual Machine (VM) on Microsoft Azure is no exception. This process involves securing the VM from potential cyber threats, ensuring data protection, and maintaining the integrity of the systems. The hardening process incorporates industry best practices to reduce vulnerability and minimize the attack surface. This write-up details the process of hardening a Windows VM in Azure.
Step 1: Creating and Configuring the Windows Virtual Machine
The first critical step in securing any system is setting up the environment. In this case, the creation of a Windows-based VM in Microsoft Azure serves as the foundation for the subsequent hardening steps.
Objective: To create a secure environment where the Windows operating system can be effectively protected.
- Action:
- The process begins by logging into the Azure Portal and initiating the creation of a new Windows Server virtual machine.
- Authentication Type: A secure password is chosen for the VM, although for production environments, SSH keys or secure methods like Multi-Factor Authentication (MFA) can be considered.
Once deployed, the VM becomes the target for security hardening measures.
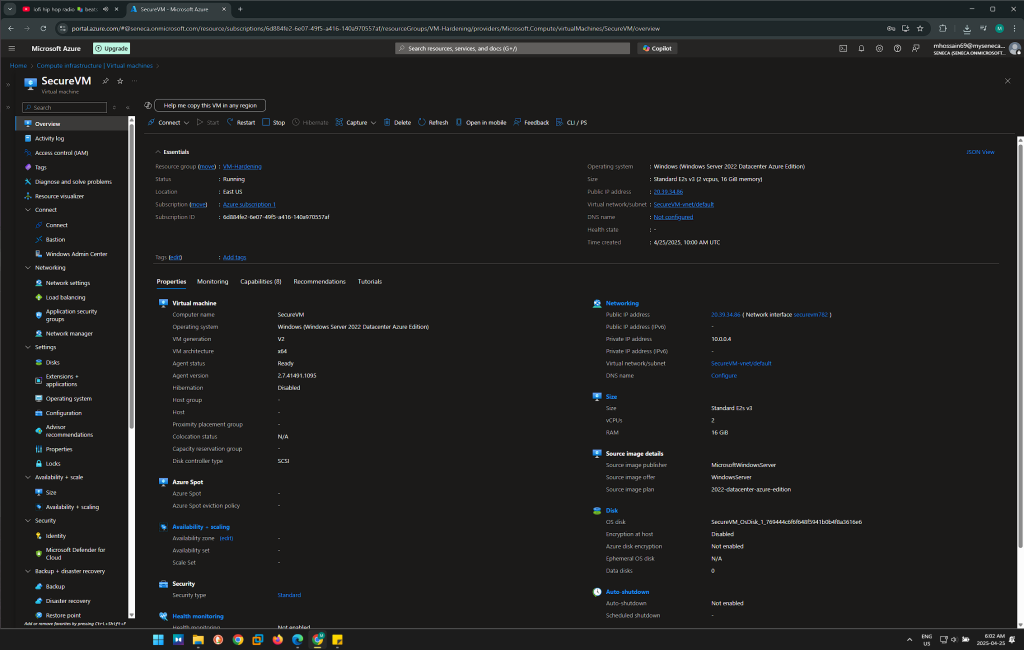
Step 2: Configuring Windows Defender Antivirus and Windows Firewall
One of the first layers of defense in securing the Windows VM involves activating built-in security tools like Windows Defender Antivirus and Windows Defender Firewall.
- Objective: To protect the VM from malware and unauthorized network traffic.
- Action:
- Windows Defender Antivirus: By default, Windows Defender Antivirus is enabled, and its real-time protection feature is turned on. Cloud-delivered protection is also enabled to provide more effective threat detection based on patterns found across global data.
- Windows Defender Firewall: The firewall is configured to block any unnecessary inbound traffic, ensuring that only trusted sources can communicate with the VM. The Advanced Security Settings section allows fine-tuning of both inbound and outbound traffic rules, further enhancing security.
These actions form a first line of defense by ensuring that the VM is protected against external and internal threats.
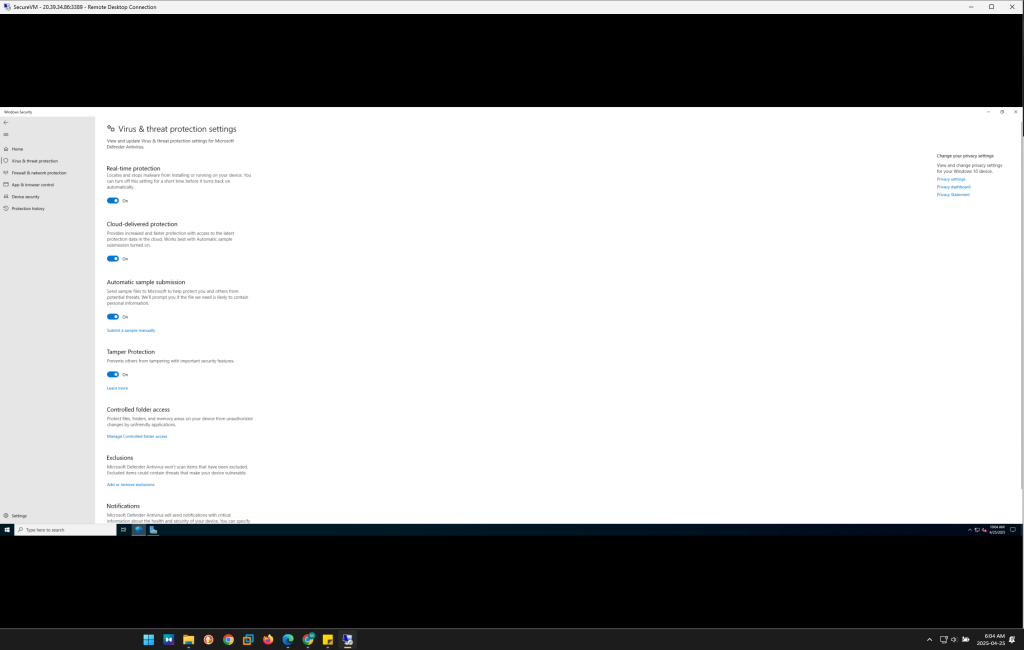
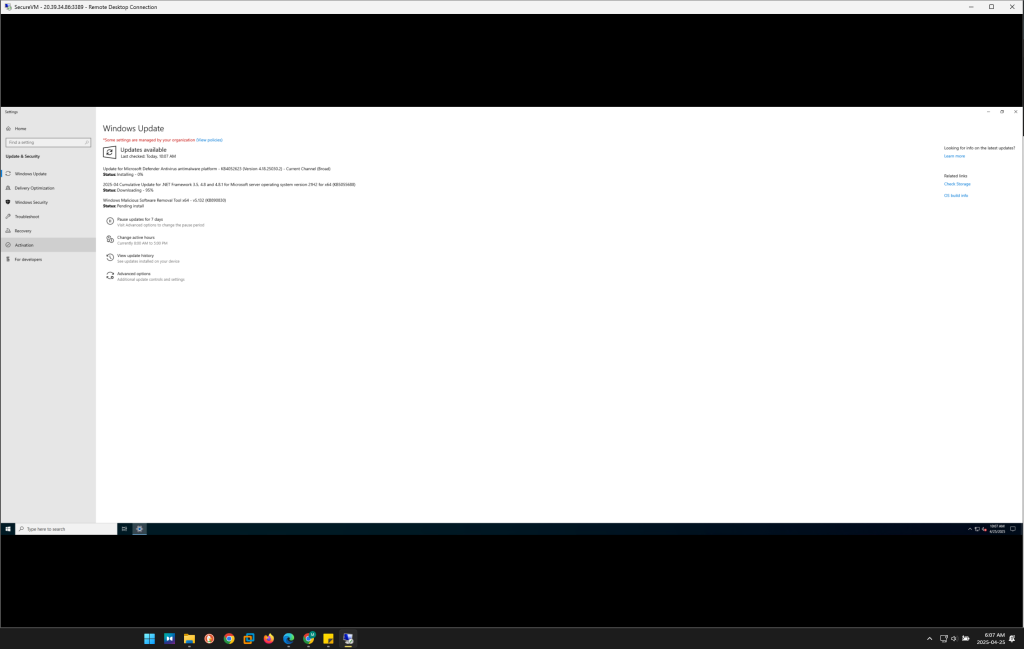
Step 3: Applying Security Updates and Patches
Keeping the system updated with the latest patches and security updates is a critical practice for maintaining a secure environment.
- Objective: To ensure that the operating system is protected from known vulnerabilities and that security patches are promptly applied.
- Action:
- Windows Update is configured to run automatically, ensuring that the system always has the latest security patches.
- Regular checks are made to ensure all critical and recommended updates are installed. The Windows Update for Business feature is also explored for environments requiring tighter control over when updates are applied, especially in larger-scale environments.
- For organizational use, Group Policy can be implemented to enforce security updates across multiple systems, ensuring compliance with security standards.
Regular updates and patches are essential to minimize the window of vulnerability.
Step 4: Minimizing the Attack Surface by Disabling Unnecessary Services
Reducing the number of services running on a system limits potential attack vectors and minimizes the system’s exposure to security risks.
Objective: To reduce the attack surface by disabling non-essential Windows services.
Action:
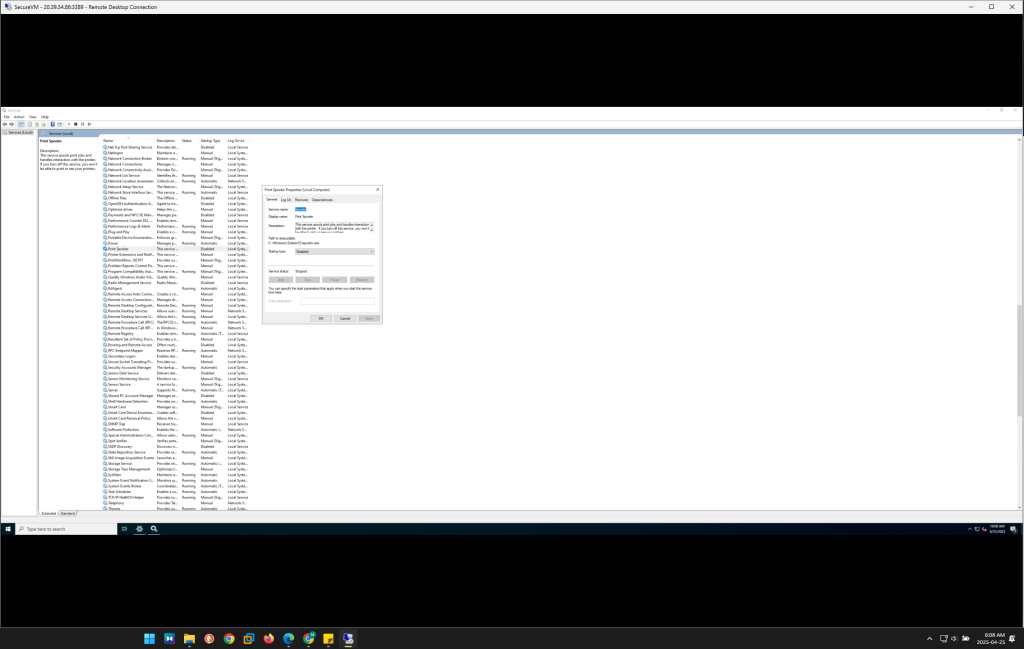
The Services Manager (
services.msc) is used to review the running services. Non-essential services, such as Print Spooler, Remote Registry, and Windows Time, are disabled or set to Manual.Specific services that are not required for the VM’s intended role are disabled to limit the number of accessible services that a potential attacker could exploit.
This hardening measure also includes disabling the SMBv1 protocol, which is known to be vulnerable to several high-profile attacks, such as EternalBlue.
Step 5: Implementing Account and Password Policies
Strong password and account management policies are essential to protect the system from unauthorized access, particularly against brute-force attacks.
Objective: To strengthen account management policies and prevent unauthorized access.
Action:
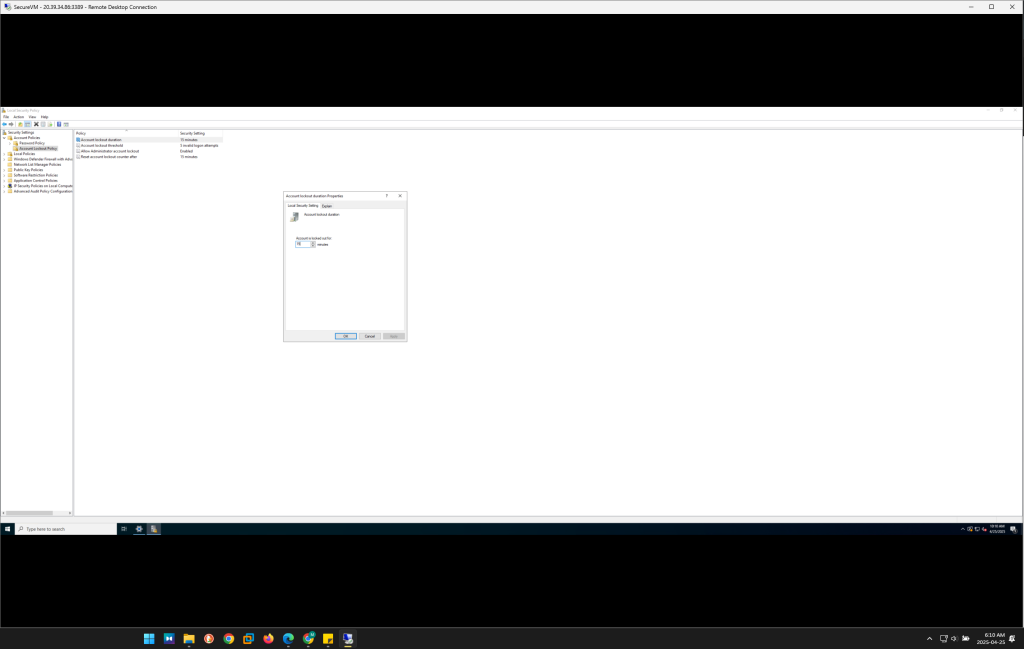
Account Lockout Policy: Configured to lock user accounts after 5 failed login attempts, with a 15-minute lockout duration to deter brute-force login attempts.
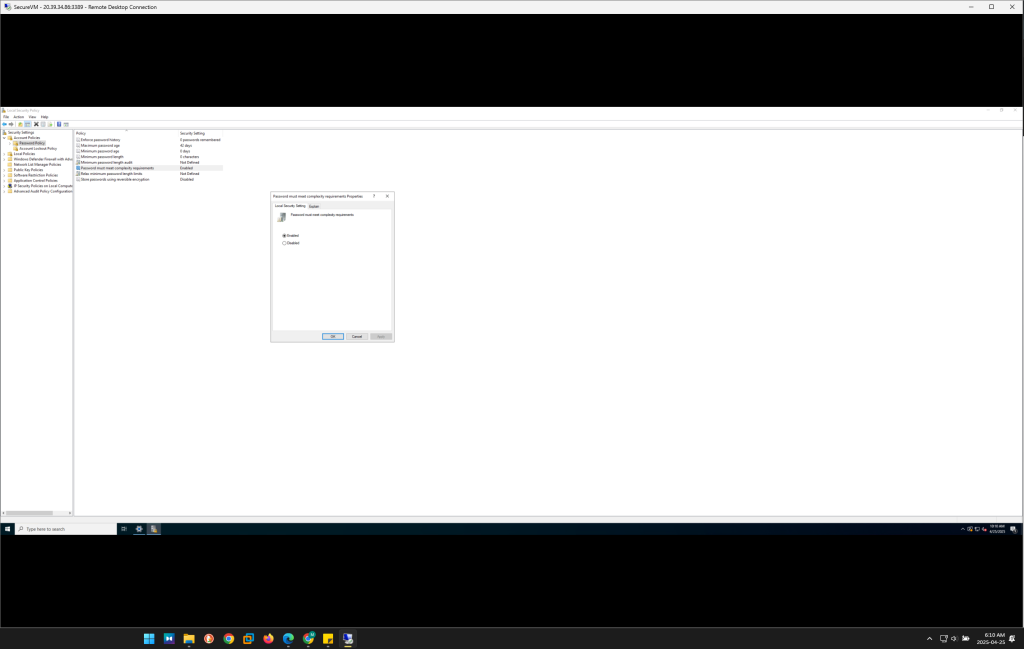
Password Policy: A minimum password length of 12 characters is enforced, and complexity requirements are set to ensure the use of uppercase letters, numbers, and special characters. Additionally, the password expiration period is set to 60 days to encourage regular password changes.
These policies are configured via Local Security Policy (
secpol.msc) and ensure that user accounts are protected from unauthorized access.
Step 6: Enabling Windows Defender Credential Guard
Credential theft, particularly Pass-the-Hash attacks, is a significant security concern. Enabling Windows Defender Credential Guard helps protect credentials from being stolen or exploited.
Objective: To protect system credentials and prevent credential theft.
Action:
Credential Guard is enabled by configuring Group Policy settings to enforce Virtualization-Based Security (VBS). This security feature isolates system secrets, such as credentials, from the operating system, ensuring that even if an attacker compromises the OS, they cannot access stored credentials.
Additionally, Device Guard is implemented to further secure the system from untrusted code execution.
By using Credential Guard, the VM’s critical authentication data is well-protected, reducing the risk of privilege escalation and credential theft.

Step 7: Setting Up Automated Backups for Data Protection
In addition to hardening the system against attacks, it is essential to ensure data recovery in case of failure or attack.
Objective: To ensure business continuity by implementing automated backups.
Action:
Azure Backup is configured to back up the VM regularly. Backup retention policies are set to ensure that critical data is recoverable in case of a security breach or system failure.
Backup tests are conducted to verify the restoration process, ensuring that data can be restored successfully when needed.
By setting up Azure Backup, the VM is protected against data loss, ensuring availability and reliability.

Step 8: Continuous Monitoring and Auditing
Continuous monitoring is essential for detecting and responding to security incidents in real-time.
Objective: To monitor the VM for signs of compromise or unusual activity.
Action:
Azure Monitor and Log Analytics are enabled to gather performance and security data from the VM.
Security logs are regularly reviewed to detect suspicious behavior, and alerts are configured to notify administrators of potential security breaches.
Continuous audits of user access and system activities are performed to ensure compliance with security policies.
By enabling Azure Monitor and Log Analytics, real-time monitoring ensures that any security incidents are promptly detected and addressed.
Conclusion
Through the process of hardening a Windows Virtual Machine on Microsoft Azure, critical security measures were implemented at every level. From configuring Windows Defender Antivirus to enabling Azure Defender, and from applying password policies to securing Remote Desktop access, each step contributes to the overall security posture of the system.
This process not only ensures the VM’s resilience against external and internal threats but also provides a foundation for proactive security measures, ensuring that the system remains secure as new threats evolve. The combination of continuous monitoring, advanced threat detection, and backup solutions ensures that the system is not only protected but also able to recover from incidents swiftly.
This comprehensive hardening process highlights the importance of securing virtualized environments in the cloud, ensuring that both the operating system and the applications running on the VM are well-protected from security breaches.